Statistics at the Command Line for Beginner Data Scientists
You don’t need Python or R to start working with data. This guide walks you through using built-in Unix utilities for real statistical analysis.
You don’t need Python or R to start working with data. This guide walks you through using built-in Unix utilities for real statistical analysis.
The behaviors that get you promoted The post How to Climb the Hidden Career Ladder of Data Science appeared first on Towards Data Science.
A new NeurIPS 2025 paper shows how self-supervised learning imbues ViT with better image understanding than supervised learning The post Do Labels Make AI Blind? Self-Supervision Solves the Age-Old Binding Problem appeared first on Towards Data Science.
For powering next-generation AI models in 2026, Bright Data’s Web Scraper API delivers on all fronts: dynamic site support, anti-bot automation, structured output, and global reach.
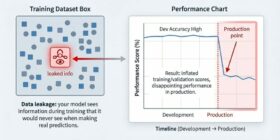
Data leakage is an often accidental problem that may happen in machine learning modeling.
Instead of catching you off-guard with a jump scare this Halloween season, EFF is here to catch you up on the latest digital rights news with our EFFector newsletter! In this issue, we’re helping you take control of your online privacy with Opt Out October; explaining the UK’s attack on encryption and why it’s bad for all users; and covering shocking new details about an abortion surveillance case in Texas. Prefer to listen in? Check out our audio […]
Sundar Pichai sits down with Logan Kilpatrick to discuss Gemini 3 on the Google AI: Release Notes podcast.
This article is divided into three parts; they are: • Understanding the Architecture of Llama or GPT Model • Creating a Llama or GPT Model for Pretraining • Variations in the Architecture The architecture of a Llama or GPT model is simply a stack of transformer blocks.

The real-time headphone translations experience keeps each speaker’s tone, emphasis, and cadence intact, so it’s easier to follow the conversation and tell who’s saying what.
Robust proxies allow you to rotate identities, reach any region, and bypass sophisticated anti-bot systems, all while protecting your infrastructure from blocks and blacklisting.